Best Practices in Finance Implementations

Blog Best Practices in Finance Implementations Achieve Financial Excellence with Dynamics 365 Finance and Operations The primary objectives of implementing Dynamics 365 Finance and Operations are to attain financial management and accounting excellence while ensuring compliance with regulatory requirements. After successful implementation, the business should be equipped to generate financial insights from any location and […]
Project Management: Be Proactive, Not Reactive

Blog Project Management: Be Proactive, Not Reactive Are you ready to elevate your project success by embracing a proactive approach instead of constantly reacting to issues? Project management is an act of anticipation, not reaction. This means that if a reaction is needed, the problem has already occurred. It may be due to scope, timeline, […]
The Significance of Identity Threat Detection & Response along with EDR

Blog The Significance of Identity Threat Detection & Response along with EDR Identity-based attacks are on the rise, and today’s organizations must detect when attackers exploit, misuse, or steal enterprise identities. Attackers are using Active Directory (AD) and credentials more frequently to advance their attacks. As organizations move to the public cloud and the number […]
Defence against Cyber Attacks should be a Board-Room priority

Blog Defence against Cyber Attacks should be a Board-Room priority Leaders Must Evolve Strategies to Protect an Expanding Digital Footprint Against Emerging Threats Attacks have both increased in number and frequency during the past six months. The implications for business would be greatest if attackers or intruders are able to breach and get beyond the […]
Defending Cyber-Attacks by Isolating Attacks at the Point of Entry

Blog Defending Cyber-Attacks by Isolating Attacks at the Point of Entry Modern security service providers help their clients to protect themselves from cyber-attacks by detecting and blocking unauthorized activity, providing a real time incident response, and protecting against backed-off assaults. As security breaches become more frequent and complex, the role of a cyber attacker has […]
Why Are AIOps Tools Essential For New Age Monitoring?

Blog Why Are AIOps Tools Essential For New Age Monitoring? Conventional monitoring provides the operations teams with critical visibility into the health of their IT systems with limited scope, but with the help of the AIOps tool, it allows the operations teams to significantly broaden their view. In a data center environment, multiple tools are […]
Identity & Access Governance – Is it a NEED or a WANT?
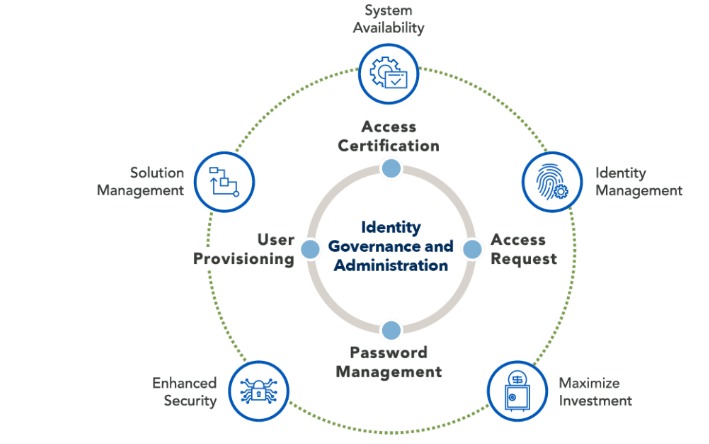
Blog Identity & Access Governance – Is it a NEED or a WANT? Identity Fraud Costs McKinsey estimates that synthetic identity fraud – in which criminals use fictitious IDs to secure credit is the fastest-growing type of financial crime in the United States. In the year 2016, synthetic identity fraud was responsible for up to […]
How to Realize Your File Requirements in Azure – Part 3

Blog How to Realize Your File Requirements in Azure – Part 3 High-Performance Computing – Challenges in the Cloud The cloud is effectively based on an agile pool of infrastructure resources – namely compute resources – that allows working environments to expand and contract as needed regardless of the size of the task at hand. […]
How to Realize Your File Requirements in Azure – Part 2

Blog How to Realize Your File Requirements in Azure – Part 2 Enterprise Database Applications – Challenges in the Cloud In order to meet mandates to get core application environments to the cloud, there comes the need to have a level of performance that is often difficult to achieve with today’s highly flexible cloud resources. […]
How to Realize Your File Requirements in Azure – Part 1

Blog How to Realize Your File Requirements in Azure – Part 1 An overview into how to solve challenges that moving to the cloud presents for file services, enterprise database applications, high-performance computing and analytics. As companies make the decision to transform IT operations by moving more of their applications1 to the cloud, they are […]
